What is a DDoS attack?
A distributed denial of service (DDoS) attack is a cyberattack designed to make a website, online service or network unavailable by flooding it with malicious traffic from multiple sources. Unlike a denial-of-service (DoS) attack from a single source, DDoS attacks use numerous devices (often harnessing tens to hundreds of thousands of attacking systems) to overwhelm targets with traffic volumes that the connecting infrastructure and systems cannot handle. When successful, these attacks prevent genuine users from accessing internet-based services, causing business disruption and potential financial losses.
How attacks play out
Attackers typically use exploitable systems – legitimate internet services that can be tricked into participating, or botnets (networks of infected computers, IoT devices and servers) to generate attack traffic. In the case of botnets, these ‘zombie’ devices are compromised without their owners’ knowledge through malware infections. The attacker controls these devices remotely, instructing them to simultaneously send requests to a target or victim. The ensuing volume of traffic overwhelms the target’s resources, or connection to the target, causing service degradation or complete failure.
Types of DDoS attacks
DDoS attacks can be categorised based on which open system interconnection (OSI) network layer they target:
Layer 3/4 (network/transport) attacks target network infrastructure by exhausting bandwidth or connection capabilities. For example:
- SYN floods exploit the transmission control protocol (TCP) handshake process. When computers connect, they use a ‘handshake’ where one sends a synchronize (SYN) request, the other acknowledges with synchronize-acknowledge (SYN-ACK) and the first completes with ACK. Attackers send many SYN requests without completing the handshake, leaving the server with partially open connections that exhaust its resources.
- UDP floods send large numbers of user datagram protocol (UDP) packets to random ports. Unlike TCP, UDP doesn’t require handshakes, making it easier to spoof. This forces the target to process each packet, overwhelming its capacity.
- ICMP floods overwhelm targets with echo request (ping) packets. Internet control message protocol (ICMP) is normally used for network diagnostics like the ‘ping’ tool, but attackers can exploit this legitimate service using it to send massive volumes of these requests or responses.
Layer 7 (application) attacks target web applications and are typically more sophisticated.
- HTTP/HTTPS floods send seemingly legitimate hypertext transfer protocol (HTTP) requests (the standard protocol for web browsing), which consume server resources. By targeting resource-intensive functions like searches or login processes, attackers can overwhelm servers with requests that appear genuine.
- Low and slow attacks (eg Slowloris) keep many connections open by sending partial HTTP requests at a deliberately slow rate. Named after the slow-moving sloth, these attacks keep connections open indefinitely with minimal bandwidth cost to the attacker, gradually occupying all available server connections.
- DNS query floods overwhelm domain name system (DNS) servers with numerous or hard-to-process requests. DNS translates human-readable domain names (like example.com) into IP addresses that computers use to locate services. By flooding these servers with malicious queries, attackers can disable this critical piece of internet infrastructure for targeted victims.
The growing DDoS threat
The scale and frequency of DDoS attacks have increased dramatically in recent years. According to industry data, attacks doubled between 2022 and 2024, with some estimates suggesting global attacks exceeded 100m in 2024 alone. This growth is driven by:
- the proliferation of poorly secured IoT devices, making botnet creation easier;
- increasing geopolitical tensions, with state-sponsored attacks becoming common;
- the rise of ‘DDoS-for-hire’ services that commoditise attack capabilities; and
- more sophisticated attack techniques that can evade traditional defences.
Exhibit 1: Number of DDoS attacks worldwide from Q123–Q424
Source: Statista
Who is targeted?
While any online service can be targeted, certain sectors face higher risks:
- IT and telecommunications (28% of attacks).
- Banking and finance (24%).
- Government and defence (15%).
- Energy and utilities (12%).
- Healthcare (7%).
Attacks are often motivated by financial extortion, political activism, competitive disruption or simply as diversionary tactics for more sophisticated breaches. Recent changes to the geopolitical landscape have resulted in a marked increase in state-sponsored attacks, which typically target critical IT infrastructure to maximise broader social and economic impact.
Mitigation approaches
Cloud DDoS protection typically uses so-called scrubbing services:
- Traffic destined for the target or victim is detected as suspicious when it exceeds normal patterns.
- It’s redirected to dedicated scrubbing centres – specialised data centres designed to filter attack traffic.
- Malicious traffic is identified and filtered out based on known attack signatures.
- Clean, legitimate traffic is then forwarded to the original destination.
While effective, this approach has limitations:
- It can introduce latency (delays) for legitimate users during the redirection process.
- Detection and redirection takes time to implement, allowing initial service disruption before cloud protection is activated.
- It often requires manual intervention or coordination by security teams.
- Short, repeated or agile attacks can be difficult to mitigate effectively as they may end before mitigation begins.
Exhibit 2: Leading DDoS protection providers
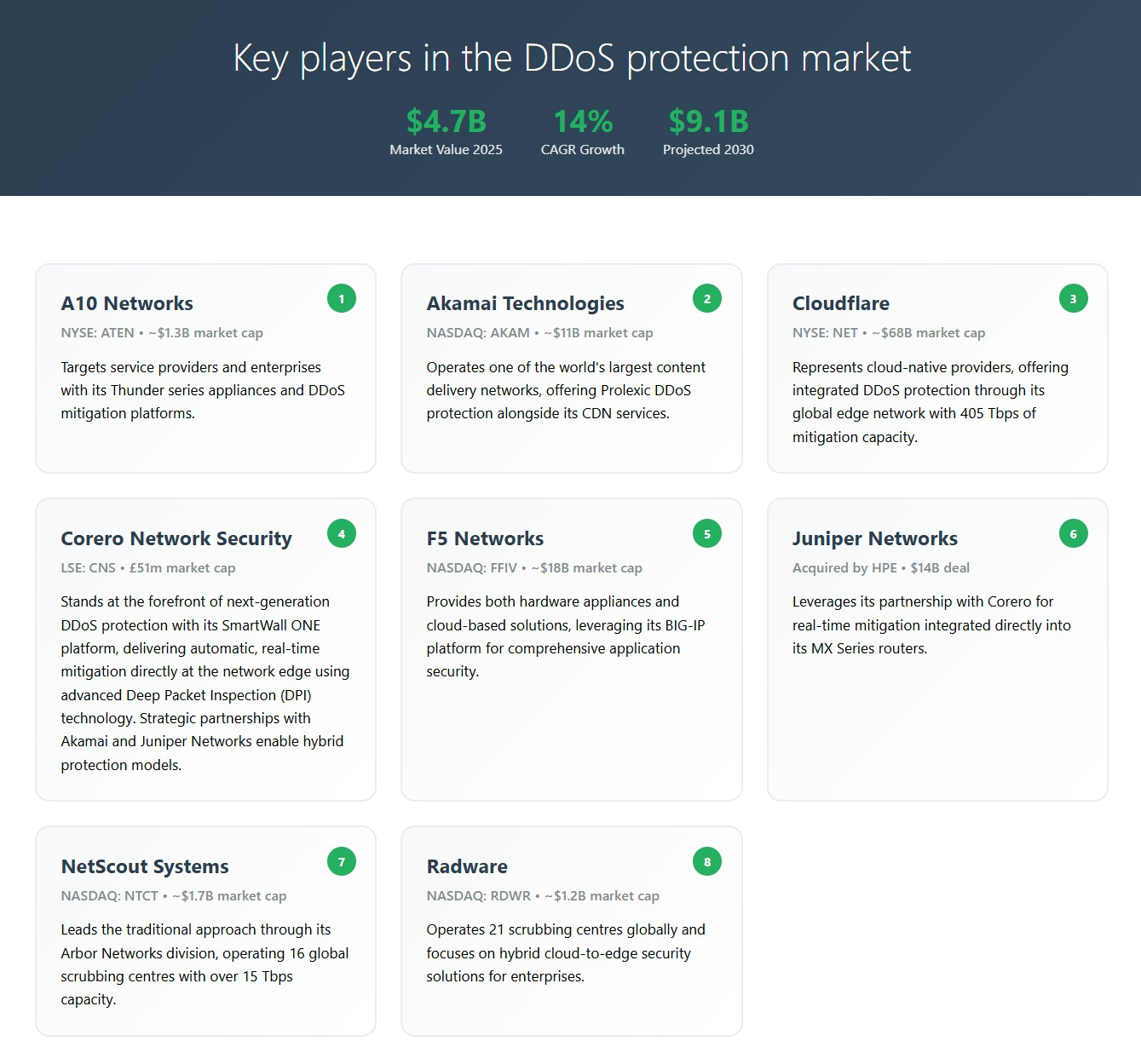
Source: Edison Investment Research
Advanced mitigation strategies
Modern DDoS protection uses more sophisticated techniques:
- Deep packet inspection (DPI): analyses the actual contents of data packets rather than just traffic patterns, enabling more accurate detection of malicious traffic. This allows security systems to examine the data being transmitted rather than just the volume or source.
- Real-time monitoring: provides continuous traffic analysis without waiting for attack thresholds to be reached, allowing for earlier detection and response.
- Hardware-agnostic solutions: software-based protection that can be implemented without changing existing network infrastructure, reducing implementation costs and complexity.
- AI/ML detection: uses artificial intelligence and machine learning algorithms to help identify anomalous traffic patterns and predict likely attack vectors.
The most effective defences combine multiple approaches in a layered security strategy, with solutions that can adapt to evolving attack methods.
DDoS as a cybersecurity imperative
As organisations increasingly rely on online services, DDoS protection has become a critical component of cybersecurity strategy. The impact of successful attacks extends beyond immediate service disruption to include:
- loss of customer trust;
- financial losses from business interruption;
- regulatory complications; and
- damage to brand reputation.
With attack volumes increasing rapidly in recent years, for example up by more than 50% in 2024, organisations must ensure their DDoS mitigation capabilities evolve to match the growing threat landscape.





